
AI-Based Hybrid Cloud Security Automation Solution Brief

AI-Based Hybrid Cloud Security Automation
Executive Summary
This solution brief introduces our AI-Based Hybrid Cloud Security Automation solution, designed to address the unique security challenges faced by organizations in hybrid cloud environments. By combining the power of artificial intelligence and automation, our solution provides advanced threat detection, security orchestration, continuous monitoring, and intelligent incident response. This brief outlines the key components, benefits, use cases, and deployment considerations of our AI-Based Hybrid Cloud Security Automation solution.
Introduction
Hybrid cloud environments offer numerous benefits in terms of flexibility and scalability, but they also introduce complex security challenges. Traditional security approaches struggle to keep pace with the dynamic nature of hybrid clouds. Our AI-Based Hybrid Cloud Security Automation solution leverages artificial intelligence, machine learning, and automation to provide proactive and adaptive security measures across hybrid cloud infrastructures.
Challenges in Hybrid Cloud Security
Securing hybrid cloud environments involves dealing with multiple cloud platforms, interconnected networks, diverse data flows, and varying security policies. Some common challenges organizations face include:
- Lack of centralized visibility and control
- Difficulty in detecting and responding to advanced threats
- Ensuring consistent security policies across multiple clouds
- Continuous monitoring for compliance and regulatory requirements
- Complex incident response and remediation processes
Key Features of Hybrid Cloud Security Software
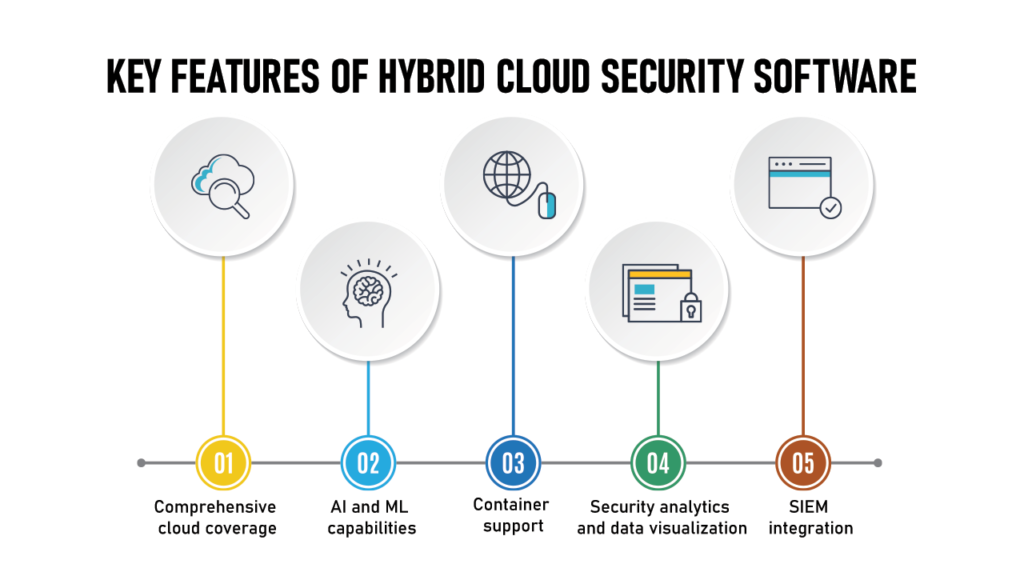
**Reference: https://www.spiceworks.com/tech/cloud/articles/top-10-hybrid-cloud-security-solution-companies/
Key Components of AI-Based Hybrid Cloud Security Automation
Threat Detection and Prevention:
Our solution employs advanced AI algorithms and machine learning techniques to detect and prevent security threats in real-time. It analyzes network traffic, log data, and behavior patterns to identify anomalies and potential security incidents. By continuously learning and adapting, the solution enhances threat detection capabilities and minimizes false positives.
Security Orchestration and Automation:
Our solution automates security tasks and workflows, reducing manual intervention and accelerating response times. It integrates with various security tools and cloud platforms to orchestrate security operations and enforce consistent policies across hybrid cloud environments. Automated incident response workflows enable rapid containment, investigation, and remediation of security incidents.
Continuous Monitoring and Compliance:
Continuous monitoring is critical for hybrid cloud security. Our solution provides real-time visibility into cloud environments, tracking configuration changes, user activity, and network traffic. It generates comprehensive reports and audits to ensure compliance with industry standards and regulatory requirements.
Intelligent Incident Response:
Our solution incorporates intelligent incident response capabilities, leveraging AI-driven analytics to prioritize and correlate security events. It streamlines incident response processes by providing actionable insights, automated playbooks, and context-rich threat intelligence. This enables efficient incident handling and reduces mean time to remediation.
Steps for Successful Cloud Security Automation
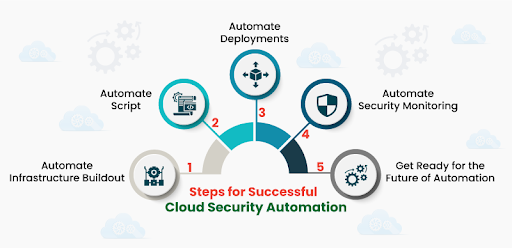
** References: https://www.veritis.com/blog/cloud-security-automation-best-practices-strategy-and-benefits/
Automate Infrastructure Buildout:
By automating infrastructure buildout, engineers are relieved from the task of manually configuring security groups, networks, user access, firewalls, DNS names, and log shipping, among others. This significantly reduces the scope for engineers to make security mistakes. Moreover, the security team need not worry about the best practices every time they spin up a new instance, as they only have to touch the scripts, not the instances, to make the changes.
Automate Script:
In traditional IT, a zero-day vulnerability or any other major security issue requires an organization’s system engineers to work rigorously to patch every server manually. But automating scripts requires only a single line change in the manifests to ensure the newly released version was running instead.
These automation script resources are declarative management tools that automatically configure instances, virtualized servers, or even bare metal servers. Whenever a new instance is launched, these scripts get the instance ready for production, including the security configuration tasks like ensuring central authentication, installing intrusion detection agents, and enabling multi-factor authentication.
Automate Deployments:
Though automating deployments is one of the best practices in DevOps implementation, it can also improve an organization’s security posture. In the event of a zero-day vulnerability, deployment automation ensures that changes made to the DevOps tool script get deployed across every instance or server automatically. This makes it possible for a single system engineer to respond to threats quickly.
Automate Security Monitoring:
In the present growing trend of hybrid and multi-cloud environments that support individual applications, it is imperative to monitor the entire infrastructure in a single interface. During an event of a security attack and downtime, it can be resource-draining and time-consuming to identify and fix the problem. Automated security monitoring aids engineers with the right intelligence to address the attack and protect critical assets.
Get Ready for the Future of Automation:
Within the next few years, data balloons and hybrid environments will become mainstream, making the manual security approach incompetent. Hence, now is the best time to develop an internal automation team or outsource it. Although achieving end-to-end process automation across hybrid environments may take months or even years, it will prove infinitely more valuable than training employees to reduce human error.
Benefits of AI-Based Hybrid Cloud Security Automation
Enhanced Threat Detection and Response:
Our solution offers proactive threat detection and rapid incident response, minimizing the impact of security breaches. AI-driven algorithms enable early detection of sophisticated threats, while automation accelerates response times, reducing the risk of data loss and business disruption.
Improved Efficiency and Scalability:
Automation simplifies security operations and eliminates manual tasks, improving operational efficiency. The solution scales seamlessly to handle large-scale hybrid cloud environments, ensuring consistent security measures across diverse workloads and cloud platforms.
Real-Time Visibility and Compliance Management:
Real-time visibility into hybrid cloud environments allows organizations to identify security gaps, enforce compliance policies, and detect anomalous activities promptly. Automated compliance checks and reporting simplify compliance management, reducing the burden on security teams.
Reduced Mean Time to Remediation:
With AI-driven incident response and automated playbooks, our solution significantly reduces the mean time to remediation. It streamlines incident investigation, containment, and recovery processes, ensuring a swift and effective response to security incidents.
Stages of Cloud Security Automation Framework
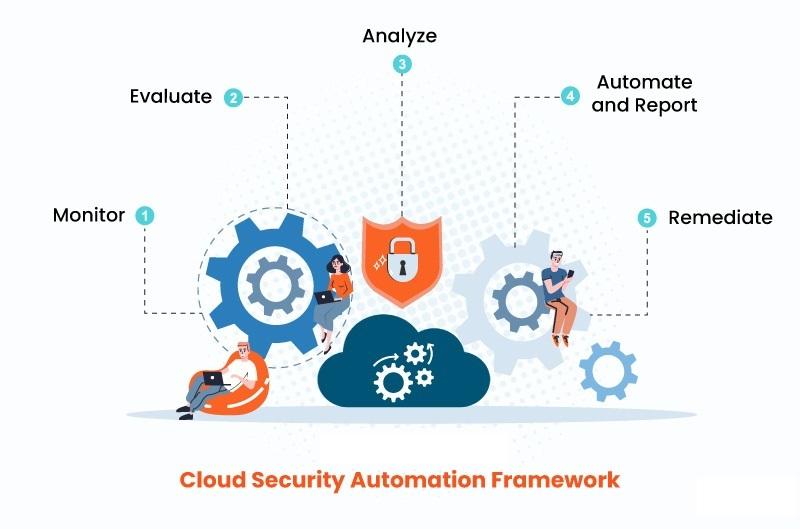
**Reference: https://www.veritis.com/blog/cloud-security-automation-best-practices-strategy-and-benefits/
Deployment Considerations
Integration with Hybrid Cloud Environments:
Our solution should seamlessly integrate with various hybrid cloud platforms, security tools, and APIs. Compatibility with major cloud providers and interoperability with existing security infrastructure ensure smooth deployment and operation.
Data Privacy and Security:
Data privacy and security are critical considerations in hybrid cloud environments. The solution should provide robust encryption, access controls, and data governance capabilities. Compliance with data protection regulations and adherence to security best practices are essential.
Training and Skill Requirements:
Organizations should assess the training and skill requirements for deploying and managing the AI-Based Hybrid Cloud Security Automation solution. Adequate training and expertise ensure effective utilization of the solution’s features and capabilities.
Conclusion
Our AI-Based Hybrid Cloud Security Automation solution offers organizations comprehensive security measures, leveraging artificial intelligence and automation. It addresses the unique challenges of hybrid cloud environments, providing advanced threat detection, security orchestration, continuous monitoring, and intelligent incident response. Real-world use cases demonstrate the value and effectiveness of our solution in securing hybrid cloud infrastructures.
© All Copyright 2023 by Fakir Technologies Ltd.
